The idea of hacking using drones has previously been just that, an idea. We’ve seen the potential of hacker drones discussed at various hacking conferences; some people have even made proof-of-concept devices. However, we’ve never seen one actually being used in the wild by cybercriminals. That is, until now.
Table of Contents
Breakdown of Events
A security researcher has provided a breakdown of the events. The incident affected a financial company on the East Coast of the U.S. They knew something was wrong when they spotted unusual activity on their internal Confluence page.
Confluence is a popular project management tool used by businesses. It is a valuable target for cyber miscreants because it contains sensitive information such as intellectual property, which could be held for ransom.
So, in the context of a hack, unusual activity on a company’s Confluence server isn’t all that unusual. What was unusual, though, was that this activity was originating on their own network. This is strange because hackers typically prefer to work remotely. Actually physically showing up in person to hack a company, Mr.Robot style, is quite rare. But this wasn’t quite the case here.
The company launched an investigation and found that an unknown Wi-Fi device had connected to their network. It was trying to cover its tracks by spoofing the MAC address of an employee.
With the help of some fancy Wi-Fi tracing equipment, they began a hunt for the offending device, which led them to the roof. There, they found two drones. The first was a DJI Phantom, a pretty standard drone you’ve probably seen before. Strapped to it was a Wi-Fi Pineapple, a popular Wi-Fi hacking tool.

The second drone was a DJI Matrice 600, which is a beast described as a ‘heavy lifting platform.’ This drone is designed to carry 6 kilos of camera equipment, though in this case, it was loaded with a Raspberry Pi, GPD Mini, 4G modem, and, of course, a bunch of batteries to power the whole setup. All in all, this equipment is estimated to have cost around $15,000.
The Plan
The plan of attack here was to use the Wi-Fi Pineapple on the smaller drone to intercept an employee’s credentials. Then, with the gear on the larger drone, they would use those credentials to log into the company’s network and access their Confluence site, all while managing the attack from miles away with the help of the 4G modem.

However, this is where we have to employ some guesswork. Due to NDAs, the exact technical details behind the hack cannot be revealed by those who investigated it.
Evil Twin Attack
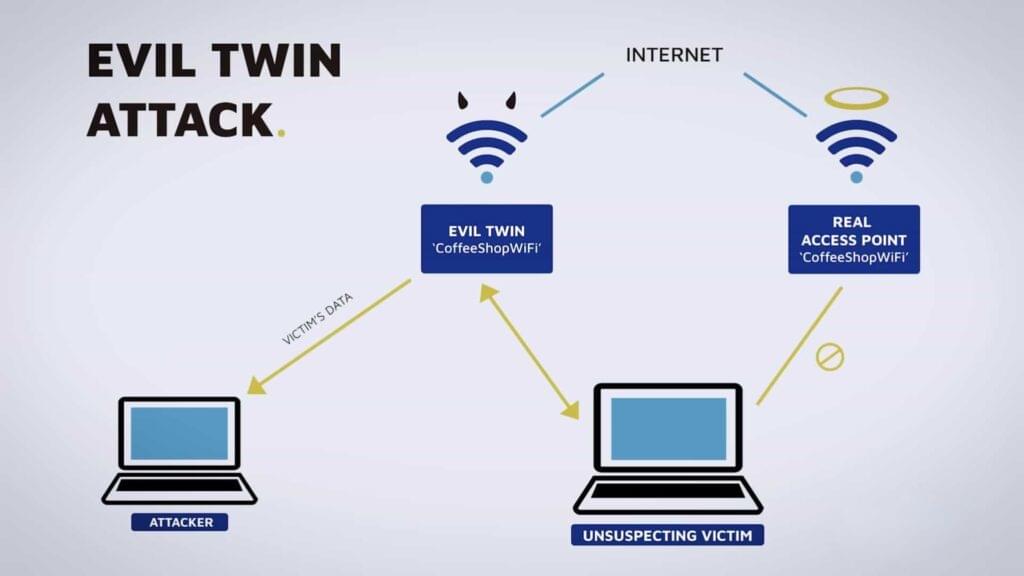
Wi-Fi attack methods are a fairly well-trodden topic. It’s likely the miscreants initially used an evil twin attack, creating a Wi-Fi network with the same name as the company’s legitimate one, and then waited for an employee to connect to it by mistake. This process could have been speed up by intentionally kicking devices off the legitimate network in what’s called a Deauth Attack, hoping that, in their frustration, an employee would connect to the imposter Wi-Fi network by mistake.
Captive Portal
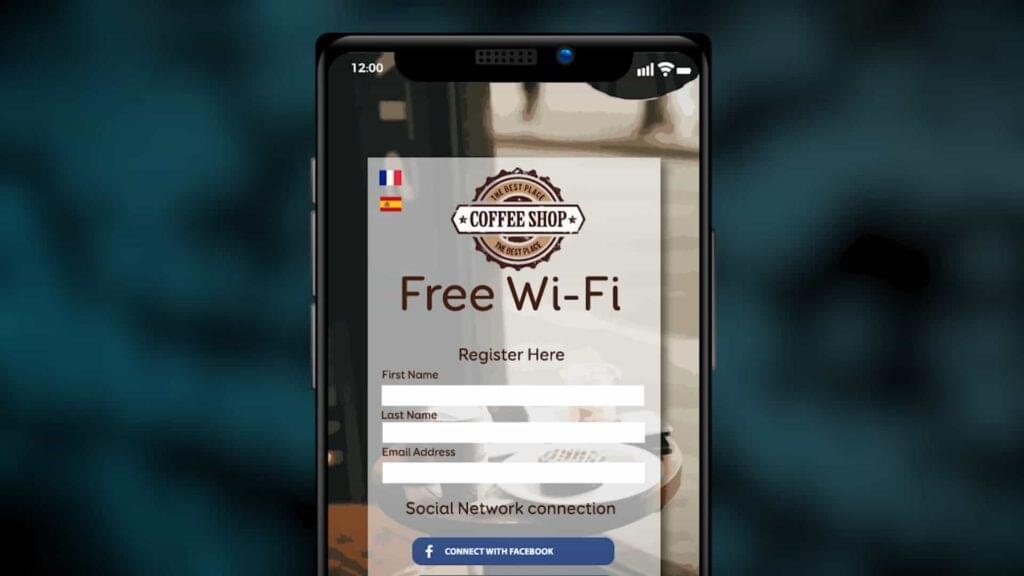
At this point, the attackers might have used a captive portal—those web pages that sometimes appear when you connect to a new Wi-Fi network. You typically encounter them when connecting to Wi-Fi hotspots at airports or coffee shops, prompting you to sign in or agree to terms. These portals can be repurposed to impersonate a genuine login page, socially engineering an employee out of their credentials.
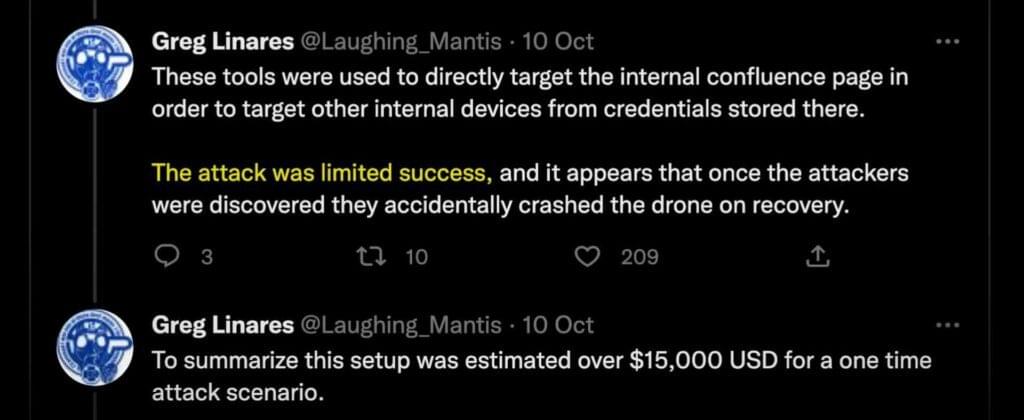
With the employee’s credentials, the attackers would have everything they needed to access the company’s services and carry out their intended actions, likely to steal data and hold it for ransom. In this case, ‘the attack was a limited success, as they did manage to access the Confluence site, but it appears they were detected before much damage could be done.
Whole Story
One thing that stood out to me about this whole story is that, while on the surface, the setup the miscreants were using seemed super high-tech and fancy, when you think about it, it was actually rather primitive and crude. It appears that the threat actors got a bit carried away and simply duct-taped all their favorite devices to whatever drone was capable of carrying that weight. The result was a very expensive, bulky, and power-hungry setup.

Skilled Threat Actors Using Hacker Drones
A more skilled threat actor would be more thoughtful about their hardware. For example, they might consider running the WiFi exploitation on a WiFi development board or a Raspberry Pi Zero. Instead of controlling it via a power-hungry 4G modem, which I imagine is very traceable back to whoever bought the data plan for it, they could use a low-power LoRa module transceiver. These devices have several kilometers of range.

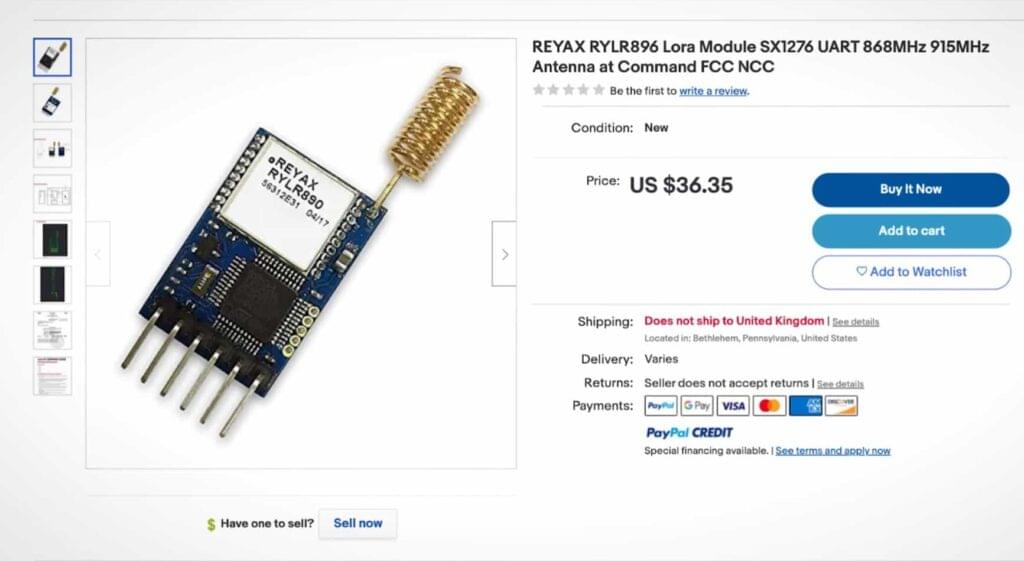
An added bonus of a setup like this is that it would be so low power that they wouldn’t need quite so many batteries. This would reduce weight further, allowing it all to be attached to a much smaller and cheaper drone. If found on a roof, it wouldn’t raise quite so much suspicion as a drone costing many thousands of dollars.
Was Ridiculous Idea
I mean, I’m not trying to give anyone any ideas here. I’m just trying to make the point that the setup the miscreants were using was really quite ridiculous. It’s as if they loaded everything but the kitchen sink onto their drones. Like, I can’t understand why they needed to strap a GPD mini laptop to the larger drone when they already had a Raspberry Pi on it. What’s the point of having a second computational device?
In the future, I think we can expect to see this kind of drone attack evolve to be a bit more sophisticated.
Source – Seytonic
Read More – DJI Mavic 3 Pro Review





